- Access to course materials
- Planning exam
- Helpful links
- Exam Handbooks
- Extra material
- Some practical hints and tips for the exam
- Just in case of bad luck
Access to course materials
PECB Kate
Kate app
Kate Web
Access via PECB profile
Access to your materials: https://pecb.com/en/login ; there will be a tab where you can see and link the registered material

Planning exam
PECB Profile > Exams
Login to your PECB Profile: https://pecb.com/en/login
In the menu on the left hand side, hit the Exams section, then “Enroll” to book an exam.

PECB Exams direct link online
To book your exam: https://pecb.com/en/eventExamList/schedule
(You’ll be asked to login to your PECB profile).
PECB Exam application
To join an exam you need to install the PECB Exams app from https://pecb.com/pecbexams/
- Windows Installer: https://pecb.com/pecbexams/PECB-Exams.exe
- MAC: https://pecb.com/pecbexams/PECB-Exams-MAC.dmg
Helpful links
Exam handbooks
Select your exam choice in the list of PECB exam, and in the right hand column, you’ll find the exam handbook.
List Of PECB Exams
In the section below, you’ll find some specific recent and popular exam handbooks, including
- NIS 2 Lead implementer & foundation
- CISO
- ISO27001 Lead Implementer
- …
PECB Exam Preparation
PECB Exam Preparation Guides: https://pecb.com/en/exam-preparation-guides
PECB Exam Rules and policies
PECB Exam Rules and Policies: https://pecb.com/en/examination-rules-and-policies
PECB Online Examinee manual (PDF)
PECB Exam platform user guide
PECB Exam Platform User Guide: https://pecb.com/help/index.php/manuals/online-exam-instructions/probo-user-guide/
PECB Exam Platform Video Tutorial: https://help.pecb.com/index.php/manual/mypecb-dashboard-manual/#3869, (4.52 onwards demonstrates the exam platform)
Exam Handbooks
NIS 2

- Lead Implementer (EN): https://pecb.com/pdf/candidate-handbooks/pecb-candidate-handbook-nis2-directive-lead-implementer.pdf
- Foundation (EN): https://pecb.com/en/education-and-certification-for-individuals/certified-nis-2-directive-lead-implementer/nis-2-directive-foundation
CISO
ISO27001
- Lead implementer (EN) : https://pecb.com/pdf/candidate-handbooks/pecb-candidate-handbook-iso-27001-lead-implementer-mc.pdf
- …
Extra material
For each exam:
Download relevant ISO standards (see chapter below) or legislation (free).
ISO Standards
- PECB store: https://store.pecb.com/search?search=&cat=15
- https://www.evs.ee/et/
- ISO store: https://www.iso.org/store.html
NIS 2
Exam Handbook
NIS2 legislation
(suggestion to print for exam)
- https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=OJ:L:2022:333:FULL).
- https://eur-lex.europa.eu/eli/dir/2022/2555
DORA
Legislation
GDPR
Legislation
Some practical hints and tips for the exam
To prepare for the exam
Open book
In case of “open book” exams you can take the learning material print (course content, TOC, index, excercises & quizes) with you , but also
- the relevant standard print (like the ISO27001 / ISO27002 standard for the ISO27001 exams)
- the relevant legislation print (NIS2, DORA, GDPR …)
- your notes
You’re not allowed to use a second pc, laptop, tablet or smart phone during the exam.
HINT: if not yet printed, print the course on paper… in advance.
Closed book
No additional help allowed, at all.
Prepare the content (open book exam)
In case of an open book exam
- you can use the KATE app during the exam to lookup content
- use the print (see previous section)
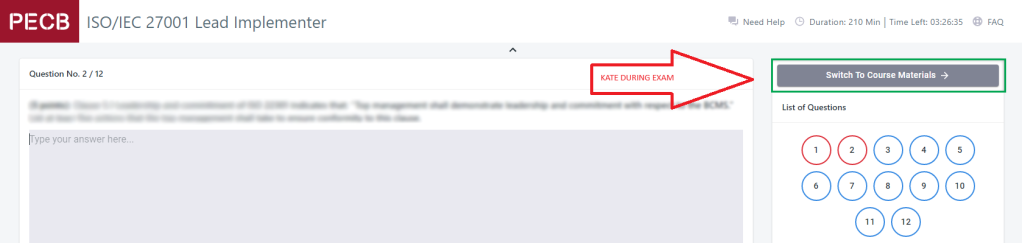
BUT, in many case people get distracted flipping screens between exam and KATE.
BETTER: print the course material (yes, less ecofriendly, but way easier and more comfortable to pass the exam).
Practical hints to prepare your open book exam
- do not memorize, but study and set up your course material for easy search
- organise your course with post-its to mark
- sections
- important topics (eg. certain articles from legislation…)

Exam app
Install the PECB exam app a few days in advance and check if it works (not a few minutes before the exam).
Please be aware that some enterprise laptops might block the installation of the app.
In rare cases, your firewall might not be happy…
If so:
- ask help from your IT department
- use a personal laptop/pc
Before entering the exam
- you can only use 1 screen and laptop/pc
- Make sure you’re in an isolated environment, without any interference from people or your phone
- Mute your mobile
- ….
Check the exam policies and conditions (see up)
Entering the exam
Check the technical conditions
- fast internet
- single screen
- no remote assistance software
- …
During the exam
Suggestion for exam approach
- Review / mark questions if you’re unsure of the answer
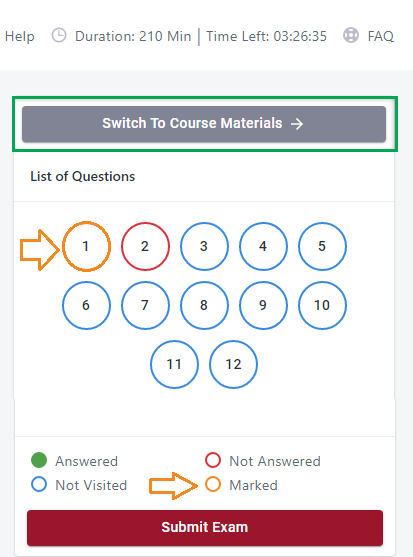
- run the exam in 3 rounds
- First round, answer the questions as quickly as possible
- mark a question for review if you are in doubt, but
- don’t loose time, don’t get stuck (waste time) on question
- Second round
- Recheck the questions you marked
- IMPORTANT: only change an answer if you know it is wrong and validated it.
- Don’t change the answer if you’re not sure.
- Third round
- answer questions you don’t know by lookng up
- lookup the answer in the course (open book exam)
- First round, answer the questions as quickly as possible
- The first time you want to submit the exam
- wait 5 minutes to hit the submit button
- review the questions, in case you can still improve your score
- only hit the submit button at second attempt
Just in case of bad luck
If exam entry fails
In case of technical issues, emergency … and you’re not able to enter exam, just know that the exam coupon is ONLY voided when you enter the exam.
Solution: Open a PECB support ticket and ask to replan exam with better conditions.
If exam result suck…
- the PECB exam coupon is valid for a free retry…
- Book a new exam with the same code
- Study again,
- ask help, eg from a coach
- Retry with success
Failure is a learning point to do better.























You must be logged in to post a comment.